Computer Systems
T2 Service Models, Application Layer: HTTP and Cookies
T2 Service Models, Application Layer: HTTP and Cookies
Renlord Yang
Service Models, Application Layer: HTTP and Cookies
- List two advantages and two disadvantages of having international standards for network protocols.
- Advantages:
- you are able to produce a system with global interoperability, without being locked into proprietary systems
- focus on interfaces
- easier maintenance and installation
- standards provide a framework that allows engineers to approach development with well defined boundaries about which layer of the stack they are interacting with - Disadvantages:
- very slow to develop, and cumbersome bureaucracy, meaning that non-standardised solutions may appear and dominate prior to any standard being released
- you may be locked into a system with inferior performance (per some metric) as a result of a) satisfying the needs of a large group rather than the specific needs of a particular project; or b) due to technology moving faster than the standards
- Suppose the algorithms used to implement the operations at layer $k$ are
changed. Do the implementations of the operations at layers $k-1$ and
$k + 1$ need to change accordingly?
- ideally, neither of the implementations would change assuming that the API on each interface does not change. However, if the implementation is not “pure” (i.e. it crosses multiple layers), then the crossed layers may also need modifications
- Suppose there is a change in the service (set of operations) provided by
layer $k$. How does this impact services at layers $k-1$ and $k + 1$?
- this will not affect layer $k-1$, since it is providing services to layer $k$, however it will affect layer $k+1$, since the services provided to it are changing
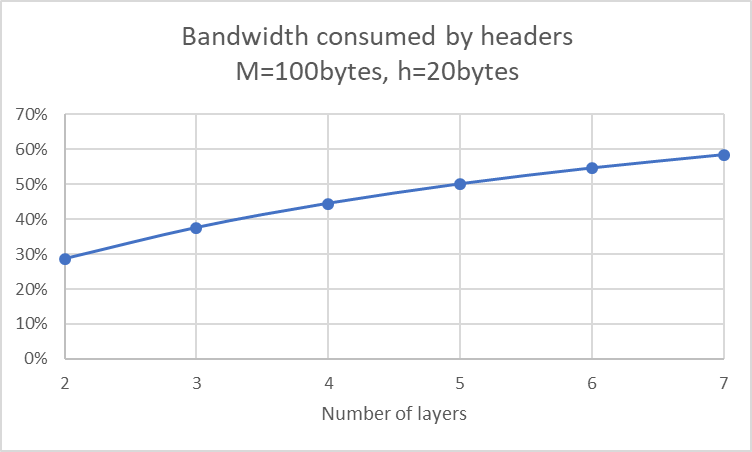
- Suppose that an application generates a message of length M bytes and
there are n lower layers each of which adds a $h$-byte header. What fraction
of the network bandwidth is filled with headers?
- $\frac{nh}{nh+M}$
Optional: To give yourself a feeling for the role of overheads,
- plot this for M = 100, h = 20 and N ranging from 2 to 7.
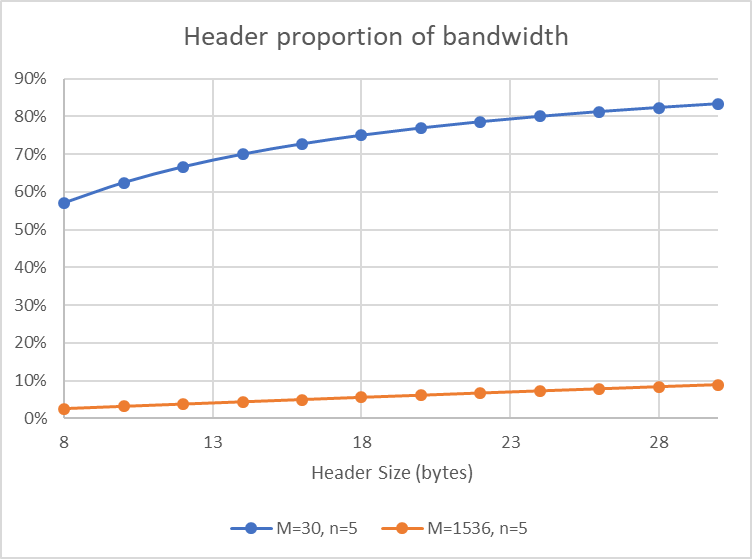
- Plot it again for M = 30, n = 5 and h ranging from 8 to 30.
- Plot it again for M = 1536, n = 5 and h ranging from 8 to 30.
- List five non-proprietary Internet applications and the application-layer
protocols that they use. (Search beyond the lecture notes.)
- File transfer e.g. FileZilla: FTP
- Any email client: SMTP
- Putty: SSH
- the web e.g. Firefox: HTTP
- time synchronisation: NTP (Network time protocol)
- network management; collating log files and modifying device behaviour: SNMP (Simple network management protocol)
- remote: telnet
- Consider an e-commerce site that wants to keep a purchase record for each
of its customers. Describe how this can be done with cookies.
- user makes HTTP GET request to website a.com
- a.com responds with HTTP response with Set-Cookie: field
- Consider the following string of ASCII characters that were captured by
Wireshark when the browser sent an HTTP GET message (i.e., this is the
actual content of an HTTP GET message). The characters $\langle cr\rangle\langle lf\rangle$ are
carriage return and line-feed characters Answer the following questions,
indicating where in the HTTP GET message below you find the answer.
```console
GET /people/index.html HTTP/1.1
Host: cis.unimelb.edu.au Connection: keep-alive Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/64.0.3282.186 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9, image/webp,image/apng,*/*;q=0.8 Accept-Encoding: gzip, deflate Accept-Language: en-AU,en;q=0.9